Windows Event ID 4769 A Kerberos service ticket was requested
Various Critical Windows 11 Event ID List HTMD Blog
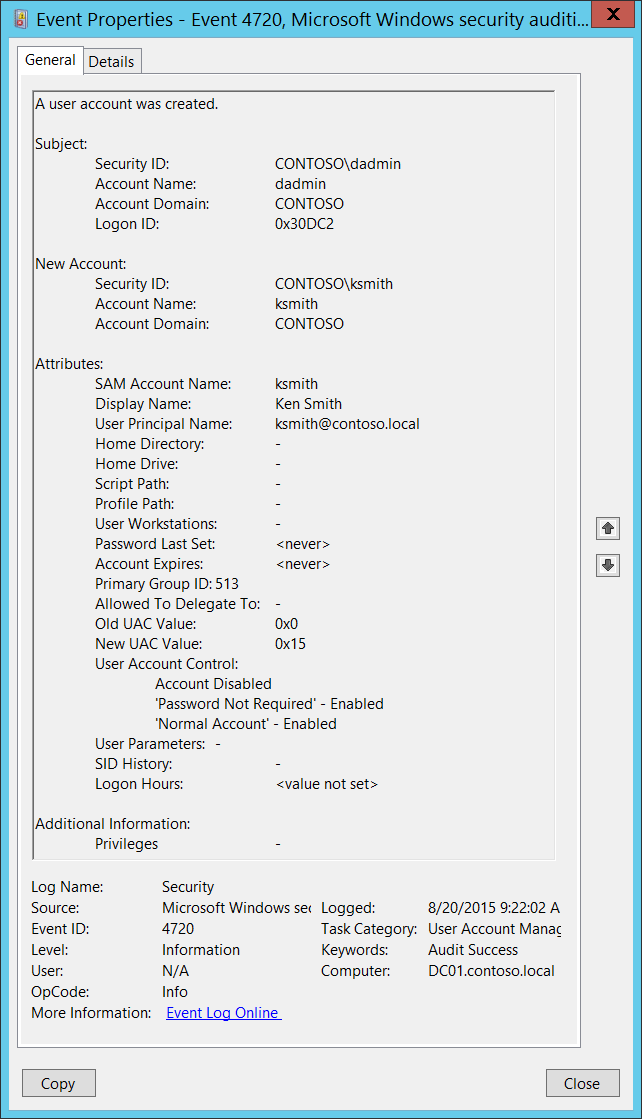
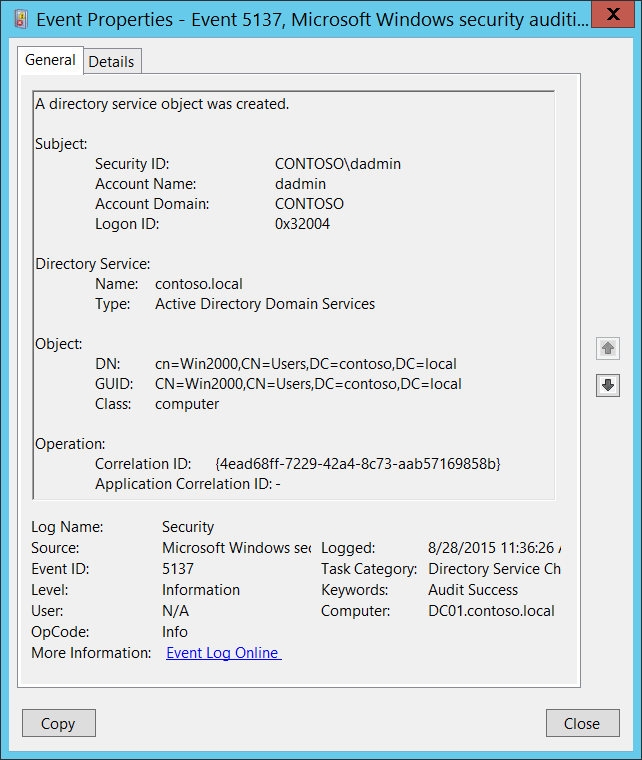
New Computer Account: Security ID [Type = SID]: SID of created computer account. Event Viewer automatically tries to resolve SIDs and show the account name. If the SID cannot be resolved, you will see the source data in the event. Account Name [Type = UnicodeString]: the name of the computer account that was created. For example: WIN81$
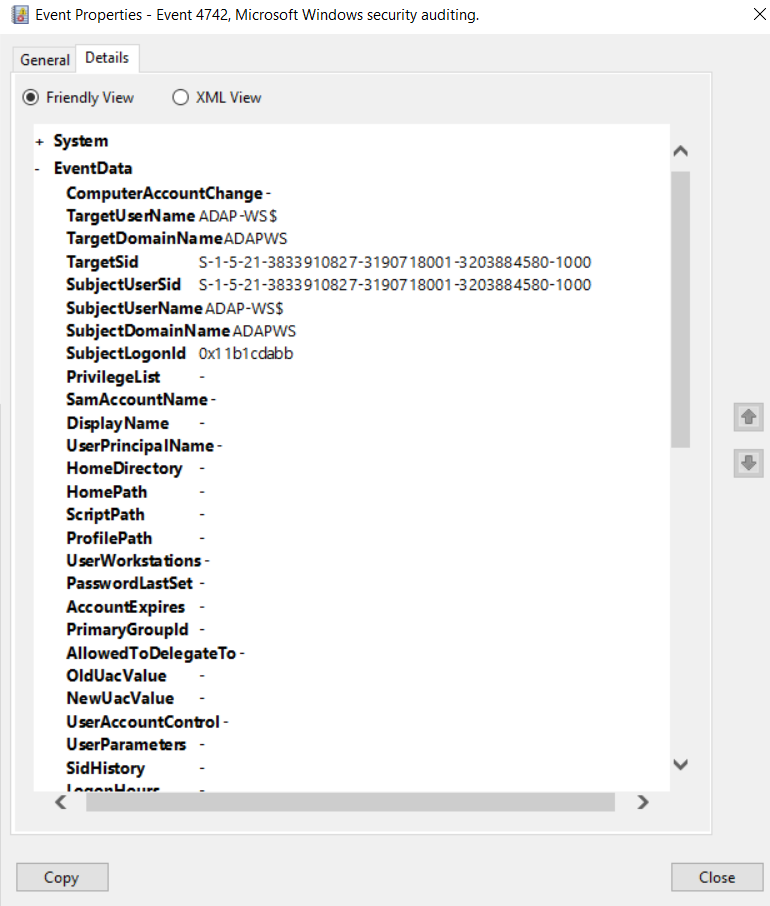
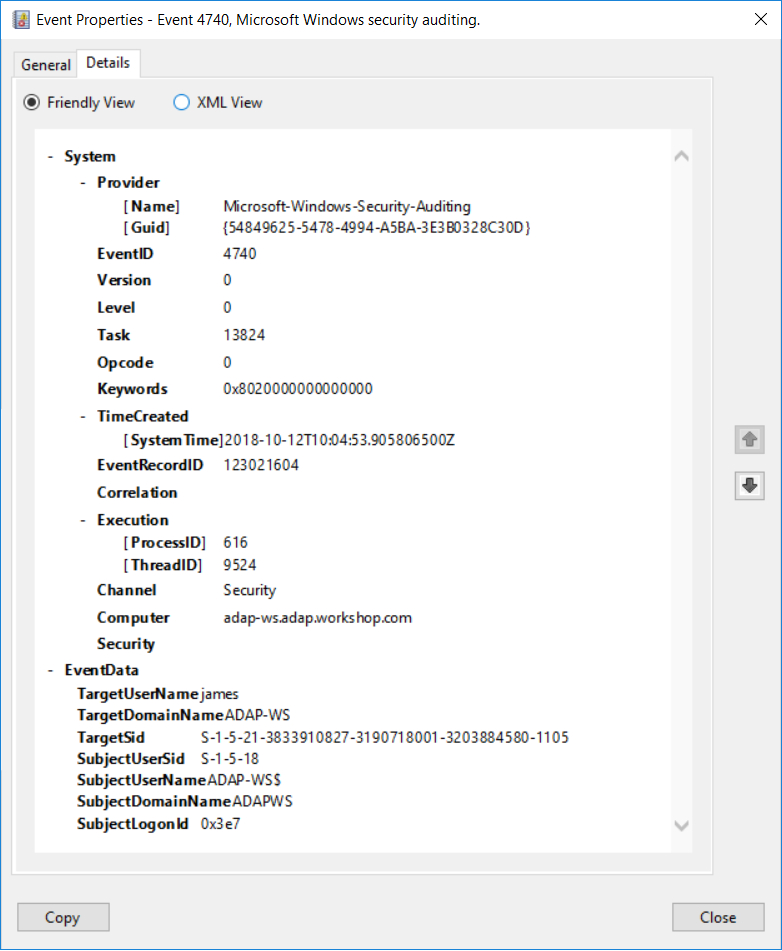
Windows Event ID 4742 A computer account was changed ADAudit Plus.
4720: A user account was created. On this page. Description of this event. Field level details. Examples. Mini-seminars on this event. The user identified by Subject: created the user identified by New Account:. Attributes show some of the properties that were set at the time the account was created. Notice account is initially disabled.
Various Critical Windows 11 Event ID List HTMD Blog
Look for Event ID 4720: A user account was created: The user identified by Subject: created the user identified by New Account:. Attributes show some of the properties that were set at the time the account was created. Notice account is initially disabled. This event is logged both for local SAM accounts and domain accounts.
Id. de evento de Windows 4740 se bloqueó una cuenta de usuario
Navigate via My Computer to. C:\Users and you will see all the user accounts listed on the local machine. You can right click the appropriate user account and go to properties and it will show you a date created, this should be the same as the creation of the user account. Just my 2 cents. Share.
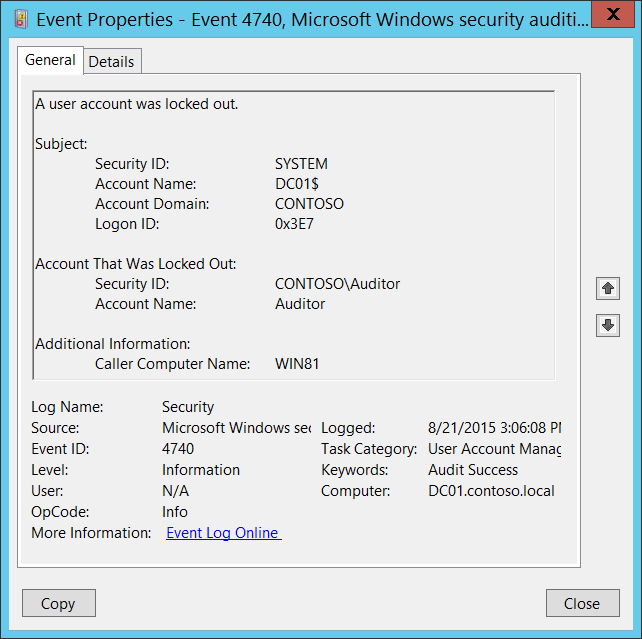
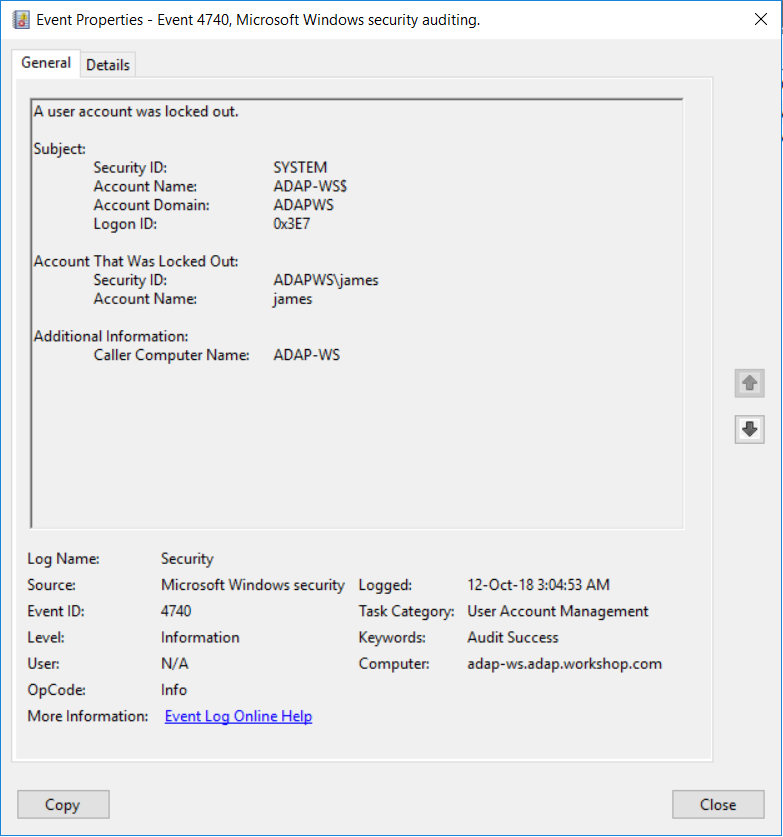
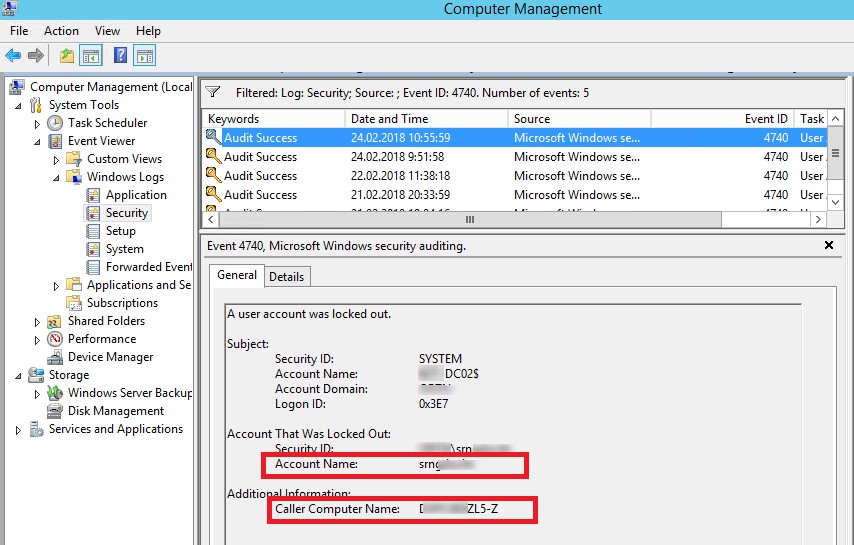
Identify Source of Active Directory Account Lockouts Troubleshooting
22 Process Command Line: Event ID 4720 - A user account was created: When a new user account is made in a windows workstation, there would be an event log with ID 4720. Since a majority of accounts are created in Active Directory, this could be an indicator of an attempt of persistence. 1 A user account was created.
Event id software install kreng
How to create AD Domain User. Right-click Users in the Active Directory Users and Computers dialogue box. Select New > User. Enter the domain user information. Click Next after the user information is configured. Enter and confirm the user password. Click Finish after you confirm the user information.
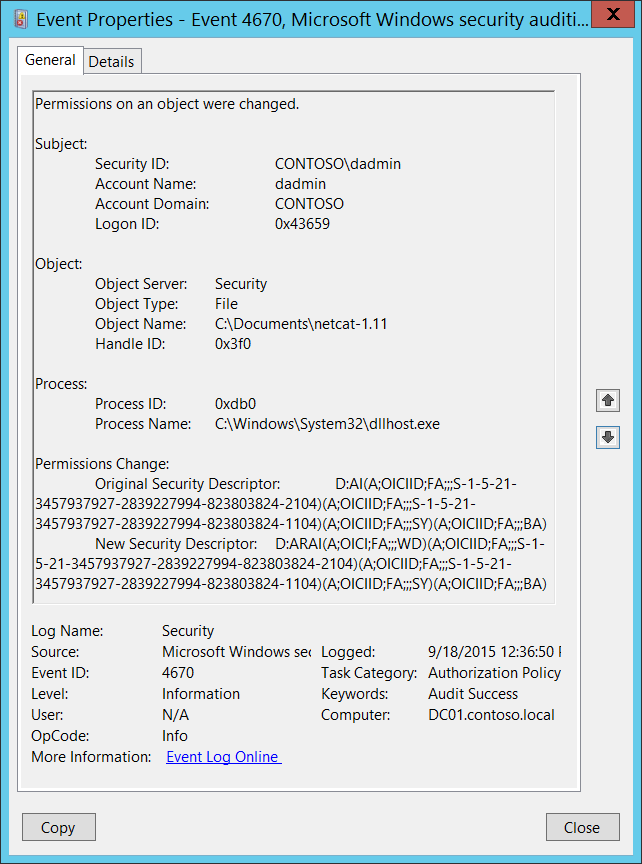
eventviewer What is the Event id for File & folder creation in Window

Security ID: The SID of the account. Account Name: The account logon name. Account Domain: The domain or - in the case of local accounts - computer name. Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events.
Various Critical Windows 11 Event ID List HTMD Blog
4722: A user account was enabled. On this page. The user identified by Subject: enabed the user identified by Target Account:. This event is logged both for local SAM accounts and domain accounts. This event is always logged after event 4720 - user account creation. You will also see event ID 4738 informing you of the same information.
Various Critical Windows 11 Event ID List HTMD Blog

We recommend monitoring all 4722 events for local accounts, because these accounts usually do not change often. This is especially relevant for critical servers, administrative workstations, and other high value assets. Describes security event 4722 (S) A user account was enabled. This event is generated when a user or computer object is enabled.
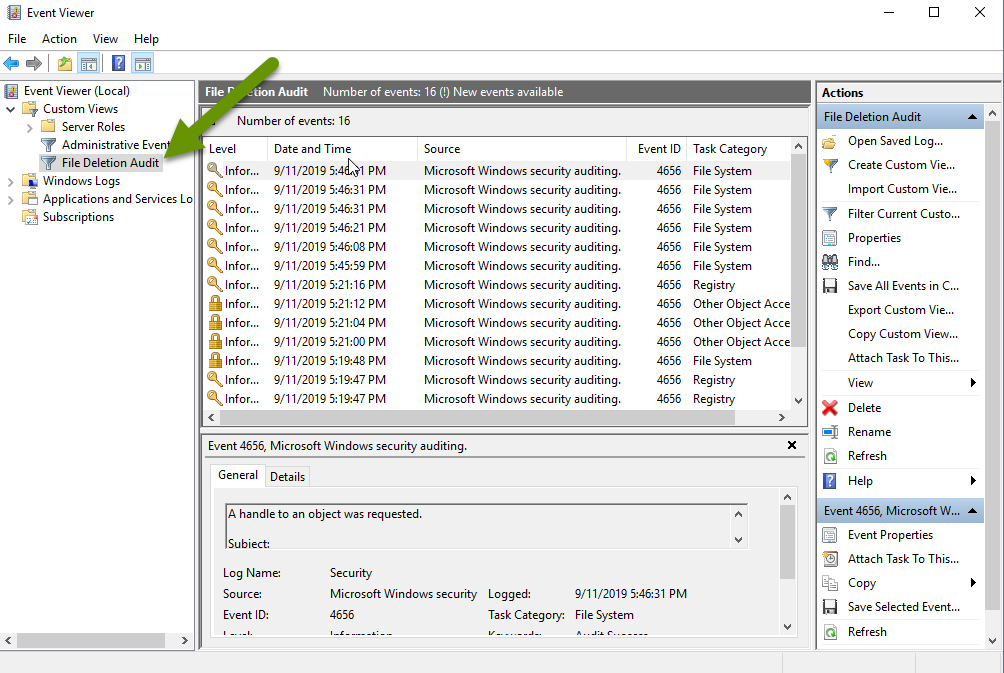
How to Track File Deletions on Windows Server Shares
I've seen these events in Event Viewer, in the Security section; yesterday was the first instance of this user account being generated with the Event ID "A user account was created", followed by some more events that seemed to 'set up' whatever this account is. one of those events has been "An attempt was made to change an account's password", and another similar one being "An attempt was made.
Various Critical Windows 11 Event ID List HTMD Blog
1. Security Event Log (Logon/Logoff Events): — Event ID 4624: Successful account logon. — Event ID 4625: Failed account logon. — Event ID 4634: An account was logged off. These events.
Id. de evento de Windows 4740 se bloqueó una cuenta de usuario
624: User Account Created On this page Description of this event ; Field level details; Examples; Mini-seminars on this event "Caller user" created "new account". This event will be accompanied by at least 2 subsequent event ID 642s and one 627. Free Security Log Resources by Randy . Free Security Log Quick Reference Chart
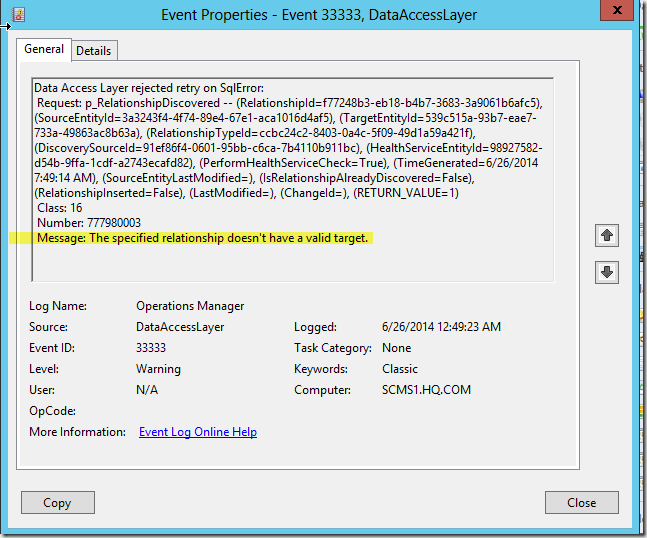
Seeing Event ID’s 10801 and 33333 on your management servers? CTGlobal
Description. Password Policy Checking API is called. When a user account is created in Active Directory, event ID 4720 is logged. This log data gives the following information: Subject: User who performed the action. Security ID. Account Name. Account Domain. Logon ID.
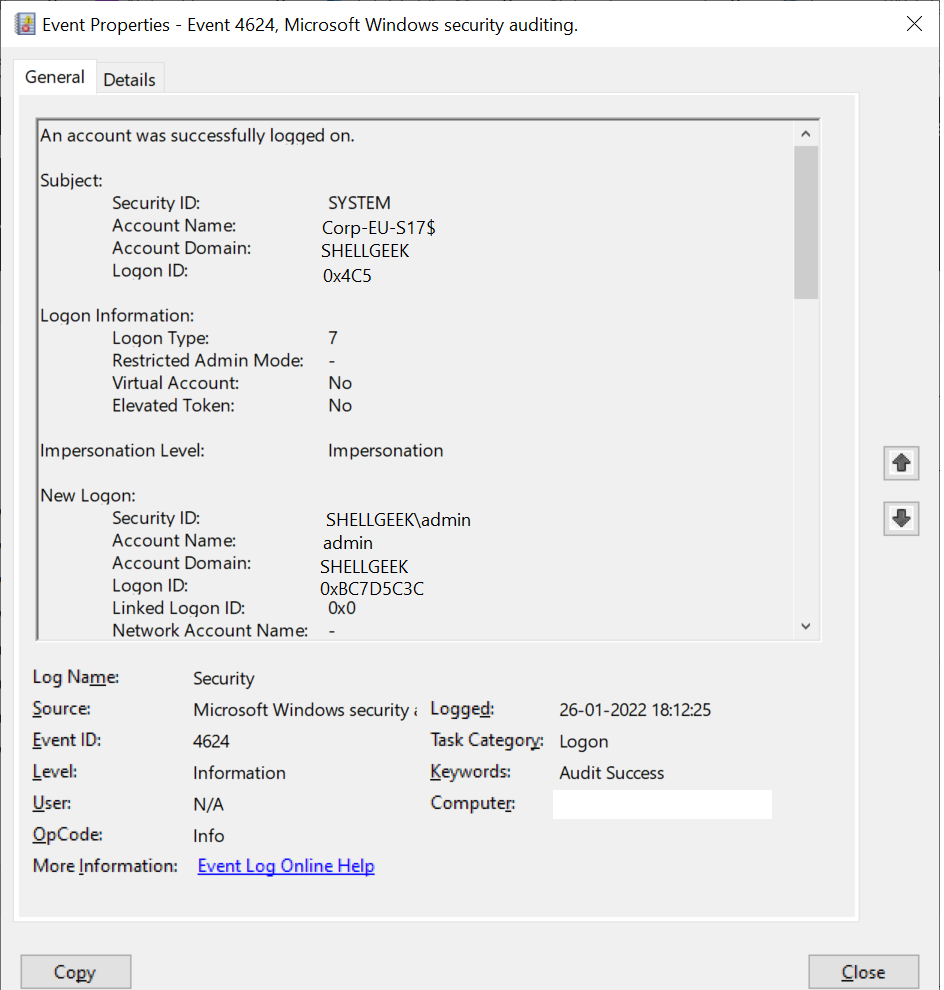
Event Id 4624 An account was successfully logged on ShellGeek
A user account was created. Subject: Security ID: %4 Account Name: %5 Account Domain: %6 Logon ID: %7 New Account: Security ID: %3 Account Name: %1 Account Domain: %2 Attributes: SAM Account Name: %9 Display Name: %10 User Principal Name: %11 Home Directory: %12 Home Drive: %13 Script Path: %14 Profile Path: %15 User Workstations: %16 Password Last Set: %17 Account Expires: %18 Primary Group.
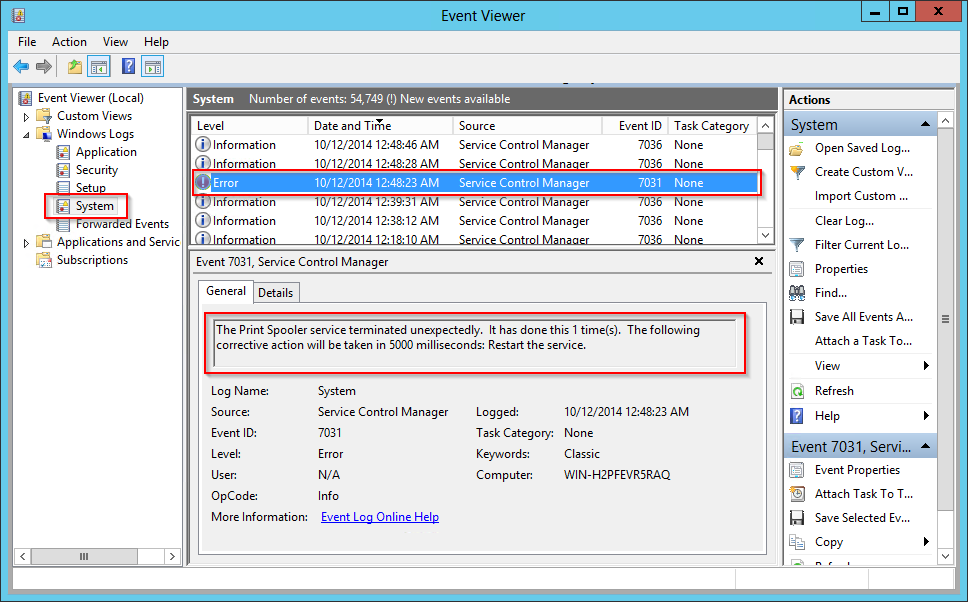
Windows Event ID 100 in the event log HowPChub
User Account Management's coverage of user account maintenance is well laid out, but be aware of one significant caveat. When you create a user account, you'll find an expected instance of event ID 4720 (User account created). But because of the way that the MMC Active Directory Users and Creators snap-in interacts with AD, you'll also see a series of event ID 4738 instances interspersed.
Getting AD Accounts Created in the Last 24 Hours Windows OS Hub
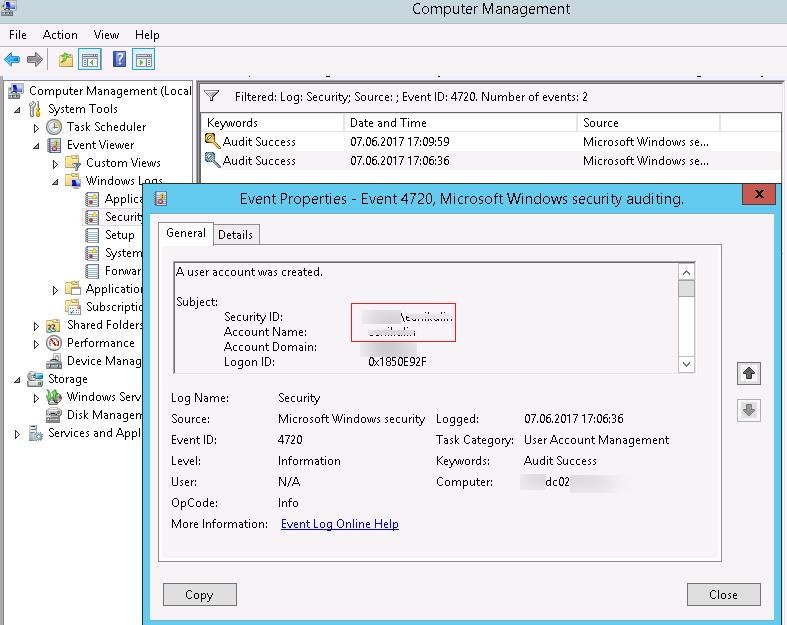
Is there an Event ID when a new LOCAL user account is created on a domain-joined computer? if so, where can I find it? I can find 4720 event ID in the domain controllers when a new user account is created in AD. However, we would like to find out if there is any log created when someone creates a local user account on our domain-joined computers.
.